[Press Release] Microservice Store Announces Security Manager (iSM) for Embedded Systems
- Murat Cakmak

- 6 days ago
- 3 min read
Updated: 3 days ago
"Proactive security and lifecycle control, built into the Embedded Microservice Runtime"
Cambridge, United Kingdom, 26 January 2026, Microservice Store today announced the integrated Security Manager (iSM), a runtime-integrated security and lifecycle layer designed to make embedded devices secure, updateable, and compliance-ready without pushing complex security responsibilities onto each product team or microservice developer.
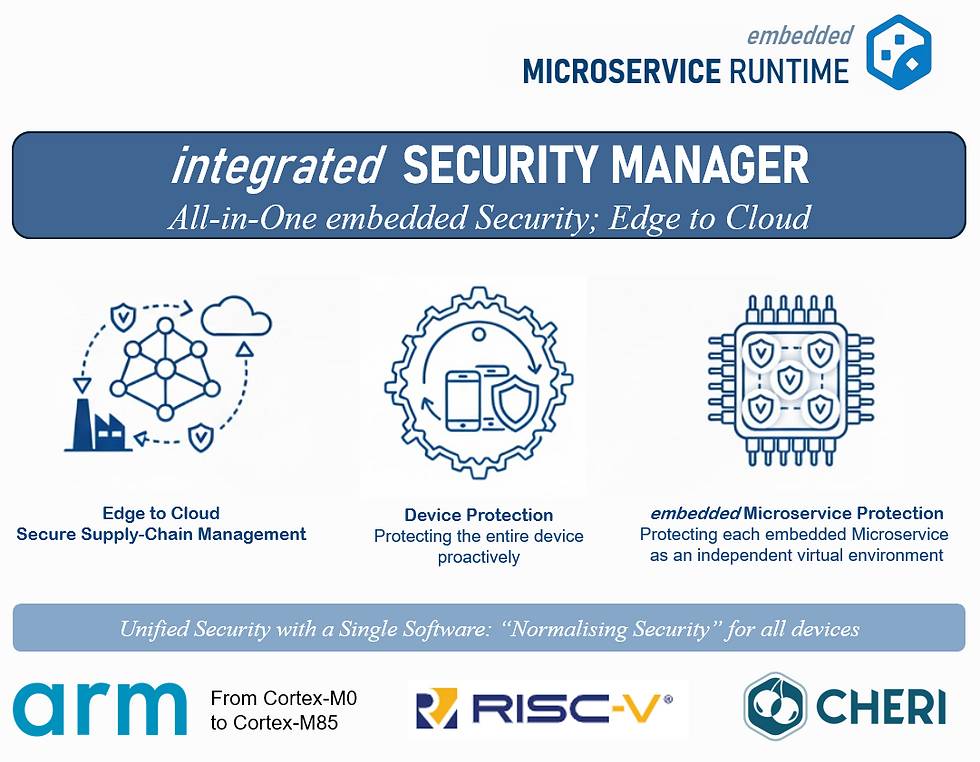
Built as part of the Embedded Microservice Runtime, iSM provides a unified security framework across both secure and non-secure hardware architectures, and extends protection from the device level down to each independently deployed microservice. By treating every microservice as an isolated, policy-governed virtual environment, iSM is designed to contain faults, limit blast radius, and keep systems operational even when a microservice malfunctions or violates expected behaviour. It normalises "Security" across all markets, unifies security across all architectures, whether secure or legacy, and is available even on the smallest Microcontrollers, such as Arm Cortex-M0.
“Connected devices are now long-lived platforms, not static firmware images,” said M Cakmak, Founder of ZAYA. “iSM is our answer to the operational reality of embedded security, proactive protection, continuous enforcement, and lifecycle control that remains consistent across architectures. It normalises strong security for every connected device, not just the traditionally ‘security-critical’ ones.”
Security enforced by the runtime, not by best-effort integration
iSM is engineered to centralise and automate core security and lifecycle requirements that are typically scattered across tooling, documentation, and bespoke implementations. It is designed to support alignment with widely adopted certification and regulatory expectations, including PSA and SESIP goals, as well as legislative requirements such as the EU Cyber Resilience Act and UK PSTI, by providing enforceable controls and operational evidence pathways.
iSM operates at three levels on the device
1) Edge-to-cloud Secure Supply Chain and Fleet management iSM supports secure onboarding and long-term fleet operations, including in-field provisioning, root credential injection, factory reset, and decommissioning. It also enables microservice-level upgrade workflows and helps produce an attestable software inventory, supporting SBOM and vulnerability reporting processes as part of a broader secure supply chain approach.
2) Device protection: A Software Security Monitor/Trusted Execution Environment
At the device level, iSM provides a consistent set of security services, including secure boot, secure update with rollback protection, secure storage, cryptographic services, unique identification, and attestation. These controls are designed to remain consistent across devices with secure execution support and those without, reducing fragmentation and security variance across product lines.
3) Microservice Protection: Microservices as Independent, Secure Virtual Environments
iSM extends device protection to each microservice: authentication at startup, independent secure upgrades, anti-rollback protection, unique identification, secure storage, and attestation for each microservice individually. When combined with the Embedded Microservice Runtime’s isolation, this enables the platform to contain and respond to violations at the microservice level.
Platform-Agnostic Access-Control with Microservice Access Policy
To simplify microservice security across architectures, iSM introduces Microservice Access Policy, a platform-agnostic permission model that specifies which peripherals, memories, and runtime services a microservice may access. Policies are default-deny and cryptographically protected (signed, encrypted, rollback-protected), enabling consistent enforcement in the field.
Automating Regulatory Compliance: EU CRA, UK PSTI
iSM is designed to make compliance truly auditable & automated, not manual. For EU CRA and UK PSTI obligations, it maintains an attested, always-current software inventory at microservice granularity, each microservice is a signed binary with a unique identity, version, cryptographic hash, declared access rights (Microservice Access Policy), and optional assurance metadata such as certification or lab assessment details. From this, iSM can generate SBOM-aligned outputs and compliance evidence, automatically capture incident telemetry, preserve forensic context, and drive coordinated vulnerability-handling workflows, including preparing structured reports suitable for CRA-aligned notification processes and accelerating vendor response, patch distribution, and audit readiness across the product lifecycle.
Availability
The Integrated Security Manager is available as part of the Embedded Microservice Runtime. Product vendors and developers can learn more and request access at Microservice Store.
Email: info@microservicestore.com
About Microservice Store
Microservice Store is a marketplace and runtime ecosystem for embedded devices, enabling plug-and-play microservices that are isolated, updateable, and governed by policy. It is designed to reduce firmware complexity, improve operational security, and create a scalable supply chain for embedded software.

![[Press Release] Embedded Microservices](https://static.wixstatic.com/media/0cfa32_16024e27fdfe44218994afce22d10327~mv2.png/v1/fill/w_980,h_653,al_c,q_90,usm_0.66_1.00_0.01,enc_avif,quality_auto/0cfa32_16024e27fdfe44218994afce22d10327~mv2.png)